This post first appeared on Risk Management Magazine. Read the original article.

Few enterprise risks are more complex, unwieldy and overwhelming than cyberrisks. A well-orchestrated cyberattack can derail business for weeks at a time and cause severe reputation damage. In preparing for such possibilities, risk managers and their colleagues in IT and security must not only focus inward on fast-changing corporate vulnerabilities, but also look outward to the vulnerabilities of third-party partners.
Now, however, a new crop of ratings firms has sprouted up that aim to assess and monitor a company’s vulnerability to cyberattacks, trying to give organizations a better idea of the risks they and their partners face.
So far, insurance carriers and brokers have been major buyers of these cyberrisk scores, using them mainly for underwriting or matching a client with a carrier’s risk appetite. Ultimately, however, these rating firms believe their primary market will be corporate risk management.
This is good news for risk managers who are looking to better understand their company’s risk profile. To assist in that effort, these cybersecurity rating firms attempt to distill a company’s cumulative cyberrisks into a simple score, much like a credit score, that can not only take into account the risk profile of the company in question, but that of its outside suppliers, vendors, cloud providers and other third parties. With this information, companies can compare past ratings and use the grades of their competitors as the impetus for improvement. This helps senior executive leaders and boards of directors get a better handle on technology risks. “Most board directors are not cyberrisk experts,” said Mike Shultz, president and CEO of ratings firm Cybernance Corp. “Trotting in the chief technology officer to outline the cyber landscape in tech-heavy jargon is like teaching calculus to first graders.”
Stephen Boyer, cofounder and chief technology officer at cybersecurity ratings provider BitSight, agreed. “We make what is a very complex cybersecurity discussion consumable for a board director or a risk manager,” he said.
Unraveling Third-Party Risks
Many boards are concerned about the prospect of a lengthy interruption of business operations due to a cyberattack. A successful cyberattack against one supplier or vendor can spread throughout the entire supply chain. An example of this risk is the massive data breach of Target’s computer network in 2014, in which hackers were able to access the retailer’s network through a heating and air conditioning contractor.
Much of BitSight’s focus is on assessing and scoring the cyber vulnerability of suppliers and other vendors that are critical to a company’s operations. “Risk managers need to look at their portfolio risk, which extends across multiple third-party partners,” Boyer said. “They need to know the vulnerability of these companies to a cyberattack and understand the resulting financial impact.”
BitSight rates the cyberrisk profile of more than 100,000 organizations worldwide, providing customers with scores on each of their suppliers and vendors, as well as a score of their aggregate risk portfolio. For example, Boyer said, “Risk managers can see that three particular suppliers are driving down their overall portfolio average, pushing them over the threshold insofar as an acceptable risk tolerance level.”
Armed with this information, the risk manager or the head of supply chain management can pressure those vendors to spruce up their cyber governance, addressing the specific vulnerabilities unearthed by the assessment. The company can then monitor suppliers’ security improvements via BitSight’s portal with a dashboard that updates the ratings on a daily basis.
Evaluating People and Processes
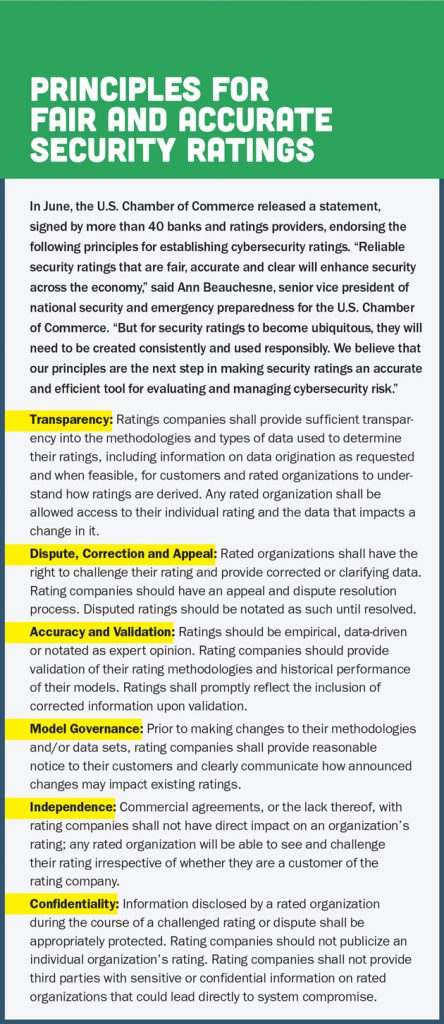 In making their assessments, cybersecurity ratings firms take into account the security of a client’s IT networks and systems. “We look at how often systems are getting compromised, how these compromises happen, how quickly they’re detected, how long they last, and the timeliness and effectiveness of the response,” Boyer said.
In making their assessments, cybersecurity ratings firms take into account the security of a client’s IT networks and systems. “We look at how often systems are getting compromised, how these compromises happen, how quickly they’re detected, how long they last, and the timeliness and effectiveness of the response,” Boyer said.
To that end, the firm examines the risk controls in place to identify and prevent botnet infections, the use of devices infected with malware, whether spam is being sent from the company’s mail servers, and user behaviors like file-sharing that may introduce malicious software into the network. These evaluations are then rolled into an overall picture of the cyber ecosystems, which is then quantified on a scale of 250 to 900. The higher the number, the better an organization’s cyberrisk posture.
RiskRecon, on the other hand, quantifies a company’s cyber resilience from zero to 10 in three categories, indicating moderate, high and critical vulnerability. Each third-party supplier or vendor is also evaluated in terms of whether or not the client should continue to do business with the organization. Toward that end, this advice is expressed as a color: green (proceed), yellow (fix), blue (limit) and red (stop).
“Our assessment tool gives you visibility across the organization and supply chain, indicating where you need to be most concerned or not concerned,” said Eric Blatte, the firm’s cofounder and president. “The overall score means nothing if you don’t know the context for the risks that have been identified.”
The firms also look beyond computer systems and networks. “If you look at a lot of recent breaches, they’re not the result of porous firewalls,” Shultz said. “The network was infected with malware because of a breakdown in policies, processes and people.
Keeping Score
For the most part, the firms tally up their scores on a noninvasive basis, meaning they are not checking out backroom servers. For example, SecurityScorecard collects open-source intelligence, surveys publicly-viewable IP addresses, deploys sensors that monitor anonymous social networks, engages in data-sharing partnerships, and listens to so-called “hacker chatter.”
“We have an outside-in perspective that reveals millions of vulnerability data points,” said Alex Heid, the firm’s chief research officer. “We then take these very complicated data sets and signals and deliver them in a way that risk managers can understand their organization’s cyber vulnerability.”
SecurityScorecard performs a 10-category tracking exercise, looking at a range of vulnerabilities including a company’s application security, network security, leaking password information and social engineering exposures. “We’re able to see every bit of software, every protocol, every report and every software version the business is running externally,” he said.
The firm subsequently compares these findings against its database of known vulnerabilities. Based on its analysis, the client’s overall cybersecurity is scored using letter grades. A company found to have zero network security risks is given the top grade of “A.” If two issues are discovered regarding, for example, the company’s social engineering exposures, the client receives a “C.” A grade of “D” denotes the bottom of the barrel. “Since we’re continuously mapping the entire internet, we’re able to recalculate the grades on a daily basis—not that they shift quickly from a ‘D’ to an ‘A’ overnight,” Heid said.
SecurityScorecard’s study of hacker chatter plays an important role in making these decisions. “Listening to the online chatter that occurs in hacking forums can speak volumes about future types of attacks and vulnerabilities,” Heid said. “Hackers love to discuss the flaws in recent attacks. We’ve amassed a database of hacker chatter going back 10 years.”
In its scoring process, Cybernance has adopted the cyberrisk resilience and risk control best practices of the National Institutes of Standards and Technology’s Cybersecurity Framework. “We’ve created software and automated packages around these best practices to examine more than 400 control points inside an organization,” Shultz said. “Using our proprietary algorithm, we’re able to gauge the adequacy of its technological defenses, procedures, policies and staff.”
This data is distilled into a score from one to 1,000, again the higher the better. Shultz said that most organizations average a score of around 350, which is actually pretty good. “To get yourself to 1,000, you would have to lock yourself in a bank vault in the mountains of Montana and not be connected to anything, while spending the entire national debt on your cybersecurity,” he said.
Like the other cyber rating firms, Cybernance provides detailed data explaining how a particular score was derived, in addition to a list of items that will help improve the grade. The firm also benchmarks customers against their competitors on an anonymous basis to see where they stand. “It’s up to the customer to decide how much risk it wants to tolerate and how much money it wants to invest to get where they want to be,” Shultz said.
RiskRecon’s scoring process assesses what it calls “severity,” calculated as the probability of a company and its systems being compromised, multiplied by the potential impact. “A company blog page that is compromised does not have the same security implications as a breach of an online banking system or the leak of a pharmaceutical product in development,” Blatte explained.
The firm begins its assessments by looking at the URLs of the customer and its suppliers, cloud providers and other third party partners. “We do an ‘auto-discovery’ of these organizations’ global IT footprints, looking at every email, server, application, domain name—literally everything you can browse about the companies on the internet,” he said.
This is not a simple exercise. “In some cases, a hundred suppliers can have thousands and thousands of IT systems, some of which are outsourced,” Blatte said. “Through our proprietary techniques, we’re able to see these companies’ entire public-facing infrastructure.”
The firm can use this to tell how often and how quickly a company patches its software, whether or not the data on its systems is encrypted, and if the company and its third-party partners are implementing global IT security standards.
These ratings firms are still relatively new to the market, but as they collect more data and scores become increasingly refined and incisive, more and more companies may start using them to help make business and risk decisions. While this information may not be able to solve the confounding puzzle of cyberrisk management, it could be a step toward more effective, stronger security.
